Data Flow Diagram For Cloud Computing Security Data Flow: Cr
Cloud computing security architecture Data security issues and challenges in cloud computing: a conceptual Data flow diagram
5 Cornerstones to a Successful Cybersecurity Program
It security solutions Cloud security: understanding the shared responsibility model layots Cloud computing network diagram where is my cloud data stored
The data security scheme for cloud computing
Cloud computing diagram stock backgroundSecurity architecture design Responsibility technologiesNetworks diagrams encryption conceptdraw system flow controls protect explain premise flowchart san defines policies communications users audit flowcharts.
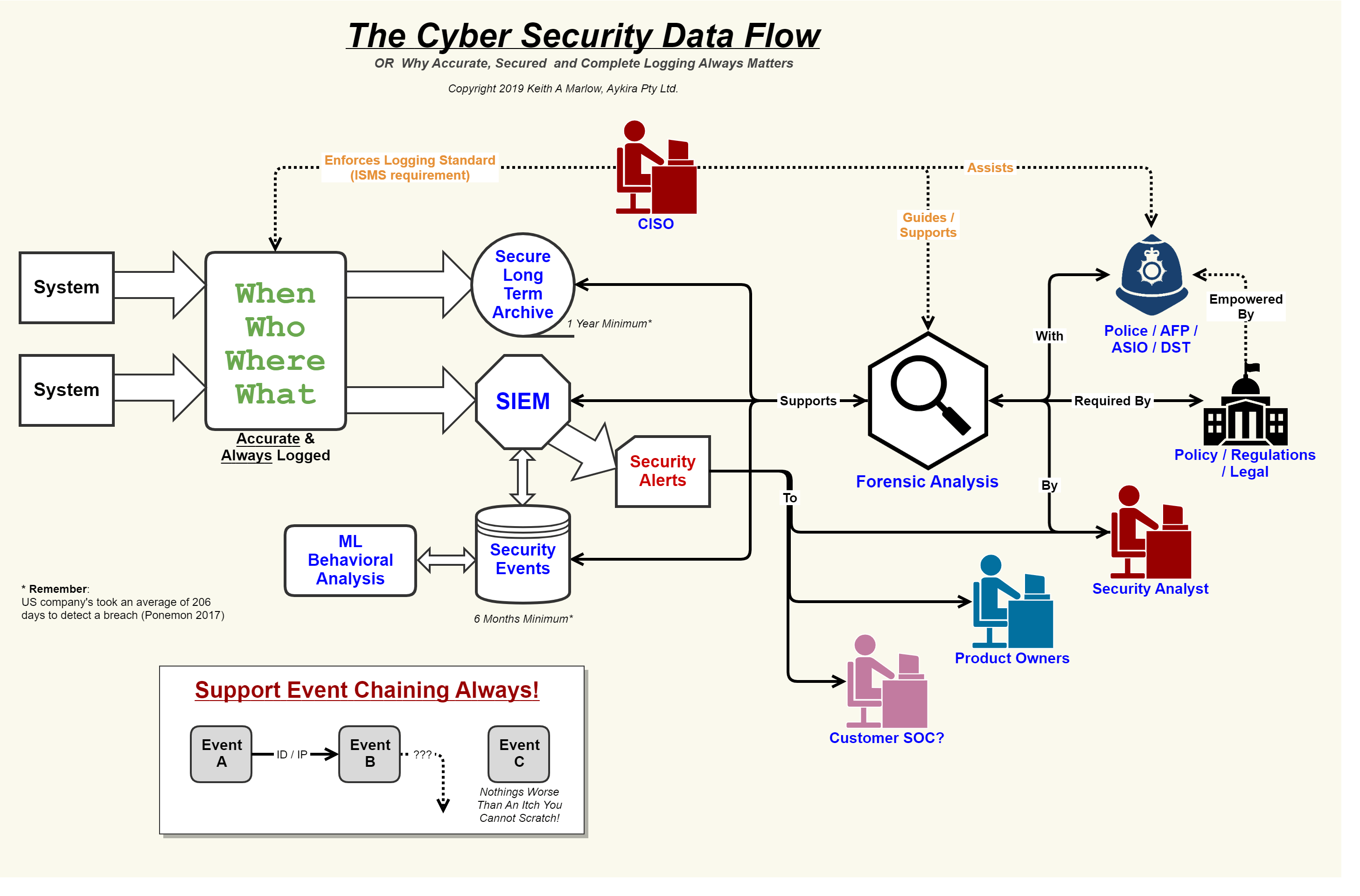
37+ data flow diagram for cloud computingSecurity network diagram architecture firewall example computer diagrams cyber clipart model networks conceptdraw recommended microsoft access examples solution devices infrastructure Security event logging, why it is so important – aykira internet solutionsData flow diagram data security, png, 1506x1128px, diagram, area.

Introduction to cloud computing architecture
Cloud computing architecture introduction example computer diagrams work networks detailsComputing inspirationseek Cloud computing diagram stock vector. illustration of mobilityGoogle cloud architecture guide.
Security architecture review of a cloud native environmentCloud nube computing connectivity workloads aws beneficios azure avantages sicherheit sicurezza compliance microsoft securing kinsta Implementation computing security adaptedSecurity microsoft cloud app access broker saas apps securing better services diagram web.

Cloud computing deployment models services diagram layout virtualization benefits network simple computer informationq
A better cloud access security broker: securing your saas cloud appsCloud computing architecture — a blueprint of cloud infrastructure Data flow diagram in software engineeringData flow diagrams.
37+ data flow diagram for cloud computingWhat is private cloud computing? Cloud computing security architecture5 cornerstones to a successful cybersecurity program.

Microsoft graph security api data flow
Data flow and security overviewSecurity flow data cyber event logging diagram internet logs important why so together showing concerning events au putting Security data flow mapping diagrams better wayCloud computing diagram.
Google cloud data big dataflow bigquery platform lifecycle capabilities compute processing services service engine stages public beta adds water simplifiedNetwork security diagrams Cloud computing security architectureCloud architecture computing infrastructure blueprint end front medium fig.

Cloud computing
Google cloud platform blog: big data, the cloud wayData flow diagram Libreoffice draw network diagram templateA comprehensive guide to cloud security.
Data flow: creating a bbm enterprise conference .